Thwarting the Midnight Blizzard Attack
Feb 14, 2024
Feb 14, 2024

3 min
Explore how Grip Security could have preempted Midnight Blizzard's recent cyberattack on Microsoft, effectively intervening at several junctures prior to the data exfiltration.
The Midnight Blizzard cyberattack on Microsoft, linked to Russia's Foreign Intelligence Service (SVR), sent shockwaves across the tech world. A seemingly innocuous breach of a forgotten, non-production test account escalated into a sophisticated operation, compromising sensitive data from the emails of Microsoft's top executives. This incident vividly illustrates that no organization, no matter how technologically advanced or security-savvy, is immune to cyber threats. It also highlights how neglected corners of IT infrastructure can become gateways to significant breaches.
Known for its sophisticated attack methods, as seen in the 2020 SolarWinds breach, Midnight Blizzard employed a nuanced strategy against Microsoft. The attackers executed a password spray attack against a legacy test account unprotected by multi-factor authentication (MFA), using residential proxy networks to mask their activities and throttling login attempts, thereby avoiding detection and account lockouts. This breach paved the way for them to exploit a legacy OAuth application with privileged access to Microsoft’s corporate environment. Their actions didn’t end there; they went on to create new OAuth applications, exploiting the compromised OAuth application to extend their access to email accounts.
Vulnerability: The attack underscores the challenges posed by SaaS sprawl, a common issue for many organizations. SaaS sprawl refers to the unchecked growth and adoption of SaaS applications, which leads to potential vulnerabilities if not properly managed. As SaaS applications multiply, the complexity of monitoring user identities and maintaining security increases, often resulting in gaps due to insufficient centralized oversight and enforcement.
Initial Access: The breach commenced with a calculated password spray attack on a non-production test account that was not secured with MFA. The attackers circumvented security measures, including account lockouts, and evaded detection by leveraging residential proxy networks and blending in with legitimate traffic.
Malicious OAuth Techniques: After securing initial access, the attackers compromised and manipulated OAuth applications to gain broad access to corporate email systems. They created additional OAuth apps with elevated permissions, leveraging the already compromised application to further entrench their access.
The breach wasn't due to a software flaw but resulted from gaps in security policy enforcement, notably a vulnerable user account due to sprawl, the lack of Multi-Factor Authentication (MFA), and insufficient management of privileged OAuth scopes. This breach's unfolding illustrates the intricate dance of exploiting these gaps, emphasizing the paramount importance of comprehensive identity management—a domain where Grip Security shines, ready to tackle every phase of such sophisticated attack chains.
Grip Security believes in leaving no stone unturned. Our platform is designed to uncover every SaaS and cloud tenant across your digital estate, shining a light on shadow SaaS applications and ensuring they're cataloged, evaluated for risk, and secured accordingly. This approach stems from the understanding that any component, big or small, could potentially serve as a gateway for cyber adversaries. This level of visibility and control could have been a game-changer in finding Microsoft’s overlooked non-production tenant.
The absence of MFA on the compromised test tenant was a crucial oversight. Grip’s platform maps your SaaS landscape to identify where MFA is missing, allowing you to enforce this essential safeguard. MFA stands as a robust barrier, one that could have significantly hindered Midnight Blizzard's entry point.
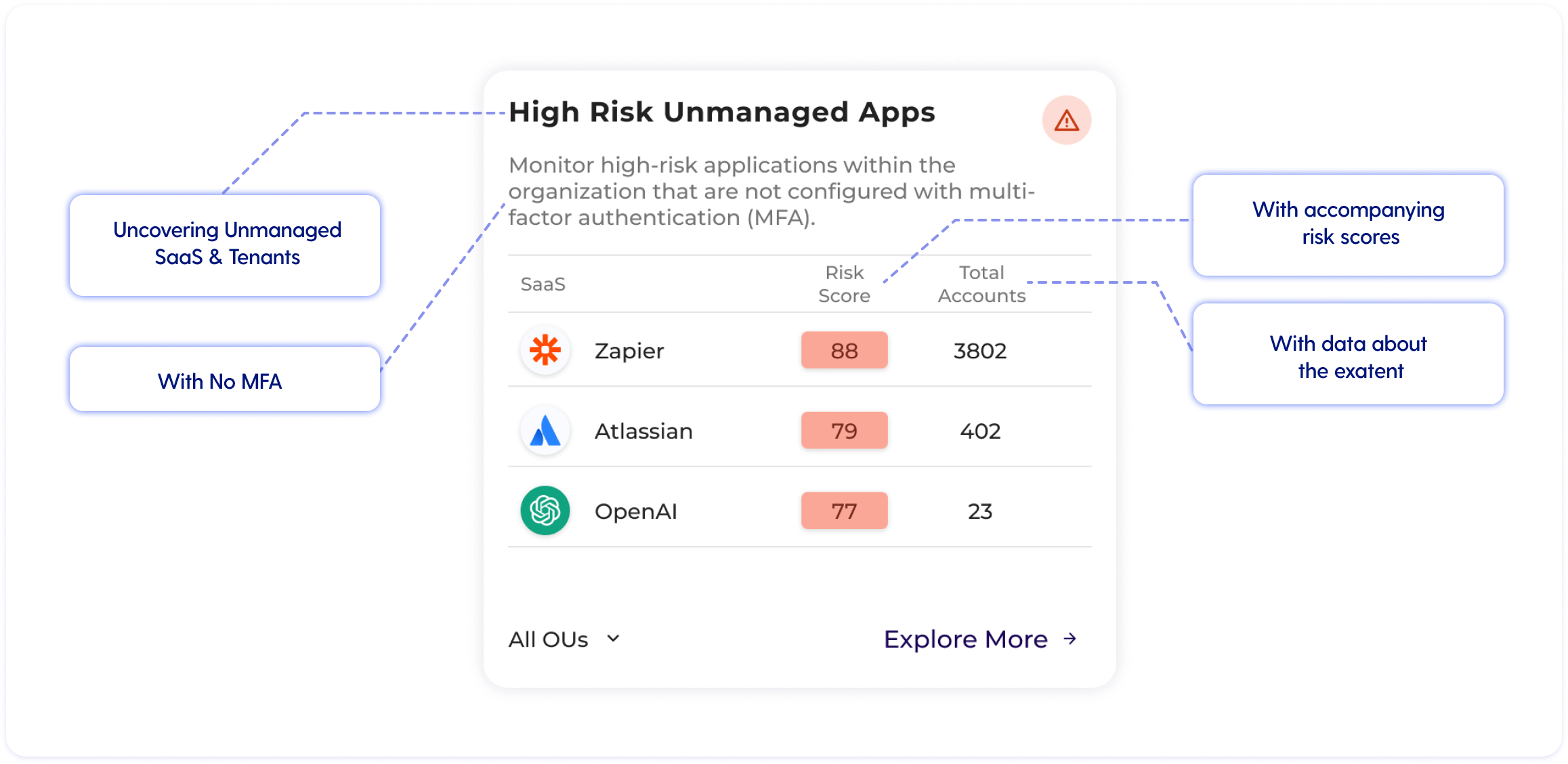
A significant aspect of the Midnight Blizzard attack was the lack of stringent management over OAuth scopes with extensive permissions. These scopes, once established, can maintain their access rights even after the initial compromise is addressed, allowing attackers to retain entry points into systems despite losing access to the originally compromised accounts. OAuth technology, while potent and versatile, introduces significant security risks and is a favored target for cyber attackers.
Heeding the advice provided in Microsoft's blog, it's recommended that organizations undertake detailed audits of OAuth privilege levels for all digital identities, including users and service principals like applications, services, and tools. This audit should particularly concentrate on identities with high-level privileges. Microsoft emphasizes the importance of context-driven reviews, such as giving extra scrutiny to privileges associated with unknown identities, those linked to inactive identities, or those that are unnecessary for the intended purpose. This nuanced approach is a specialty of Grip Security, which emphasizes access, authentication, and organizational context.
Grip Security proactively addresses these challenges with a comprehensive strategy for managing OAuth scopes. Our solution offers detailed insights into the access levels and permissions of OAuth applications, with a keen focus on critical platforms like Google Workspace and Microsoft 365. This capability is essential for pinpointing scopes that are too permissive and could be exploited by adversaries.
One of the standout features of Grip Security's approach is the proactive offboarding workflow. This process ensures that when a user leaves the organization, Grip will revoke not only the user's access to credential-based applications but also any OAuth scopes associated with Google Workspace and Microsoft 365 that the user had authorized. This approach ensures that these permissions do not remain active and pose a risk long after the user has departed from the organization.
Moreover, Grip Security extends its visibility to encompass not only user-granted scopes but also the scopes that applications extend to one another. This aspect of inter-application permissions is frequently neglected but can constitute a substantial risk if improperly managed. By offering a thorough view of OAuth interactions, Grip Security equips organizations with the tools to more effectively oversee and mitigate these security risks.
The Midnight Blizzard attack spotlights the dangers of shadow SaaS and the resulting SaaS sprawl. Grip Security brings these hidden dangers into focus, highlighting where enhanced security measures like MFA and strict OAuth permissions management can fortify defenses. Ready to uncover and mitigate your organization's hidden risks? Begin with Grip Security's free SaaS Identity Risk Assessment, a vital step towards identifying and resolving shadow SaaS risks.


Gain a complete view of your SaaS usage—including shadow SaaS and rogue cloud accounts—from an identity-centric viewpoint. See how Grip can improve the security of your enterprise.


Fill out the form and we’ll send you our Datasheet.

Give us a test drive.
Fill out the form and we’ll get in touch with you.

Fill out the form and watch webinar's video.
